Cloud Security
Paramount's Cloud Security solutions provide comprehensive protection across devices, identities, applications, and workloads, ensuring secure connections for customers
in the cloud.
Bolster organizational resilience amidst expanding digital ecosystems, hybrid work models, and evolving threat landscapes
Trust the right expert
Get Free Consultation
Trust the right expert
Get Free Consultation
Trust the right expert
Get Free Consultation

For nearly three decades, Paramount has been a trusted cybersecurity leader in the Middle East.
Our vision is to drive innovation and safeguard the digital landscape through customer insight, industry foresight, collaboration, and execution.

Expert teams with local Middle East presence, excelling in GCC laws and cybersecurity trends
Empowering businesses with robust processes to fortify cybersecurity defenses.
Integrating advanced tech & tailored security services for proactive protection
Expert teams with local Middle East presence, excelling in GCC laws and cybersecurity trends
Empowering businesses with robust processes to fortify cybersecurity defenses.
Integrating advanced tech & tailored security services for proactive protection






Paramount's Cloud Security solutions provide comprehensive protection across devices, identities, applications, and workloads, ensuring secure connections for customers
in the cloud.

Paramount's comprehensive data protection solutions - DLP, encryption, and DRM, coupled with expert implementation, safeguard organizations against threats while maintaining business continuity.

As enterprises grapple with the complexity of "On-Prem," "Cloud," and "SaaS services we help optimize Identity Governance and Access Management, through future-proof frameworks leveraging innovative technologies.
To protect critical services, users, and devices, across the network, Paramount offers industry-leading solutions, technology, and expertise (Defense in Depth (DID) approach) irrespective of organization size.

Paramount's Data Privacy consulting service provides tailored solutions by automating processes to ensure compliance with various privacy laws, including PDPL.

Paramount streamlines the complex process of implementing GRC programs by tailoring solutions with market expertise providing a unique and valuable customer experience.

As a trusted OT Security System Integrator, we provide tailored cybersecurity solutions, addressing technical, organizational, and procedural risks in operating technologies.

Offering a comprehensive portfolio across strategy, technical, and operational domains, Paramount's approach aligns with industry best practices and standards.
Over 50 skilled and certified professionals collaborate seamlessly with the Paramount SOC team, delivering unparalleled services to keep you ahead of cyber threats in today's dynamic landscape
Customers trust us with their biggest
cybersecurity challenges
Customers trust us with their biggest
cybersecurity challenges



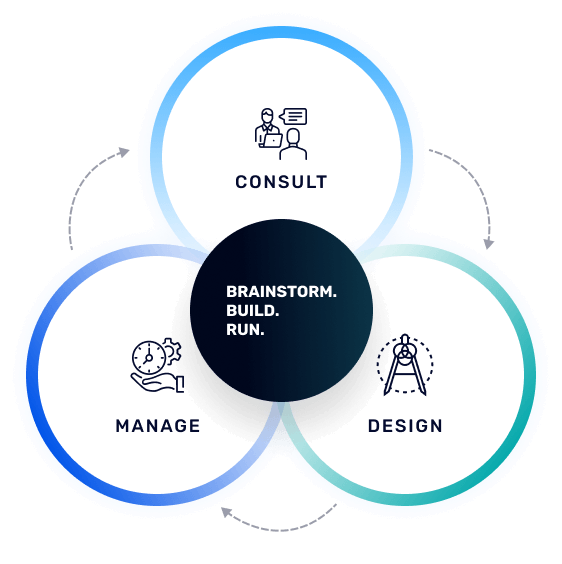
Paramountassure safeguards your organization with comprehensive cybersecurity solutions. Our expert team consults, manages, and implements the perfect security measures for your needs, encompassing network, cloud, and data protection. We go beyond security, offering data privacy and GRC solutions tailored to meet evolving international governance, regulatory, and compliance standards. With our experienced team by your side, you'll stay ahead of the curve in the ever-changing regulatory landscape.
Paramount leverages a robust suite of strategies to stay ahead of cybersecurity threats, drawing from extensive experience across various security domains. Our expertise spans Network Security, Infra Security, Data Security, Cloud Security, MSS Services, Consulting services, and IoT Security. Through proactive threat intelligence gathering, continuous training, and collaborative partnerships, we ensure comprehensive protection for our clients' digital assets, providing tailored solutions to safeguard against evolving cyber threats.
Paramount employs a multi-faceted approach to secure sensitive data and intellectual property, aligning with various regulatory frameworks and industry standards across the UAE and GCC regions. Through meticulous adherence to standards such as the National Electronic Security Authority (NESA) requirements, Saudi Arabian Monetary Authority (SAMA) regulations, and Abu Dhabi Global Market (ADGM) guidelines, Paramount ensures that critical information infrastructure and financial institutions meet stringent cybersecurity and risk management criteria. Additionally, Paramount tailors its cybersecurity solutions to comply with the Central Bank of UAE's framework and GCC-wide regulatory mandates, including those of Kuwait and Qatar, fostering seamless compliance and robust protection for multinational corporations. Furthermore, Paramount's expertise extends to the healthcare sector, where it offers tailored cybersecurity solutions to meet the Abu Dhabi Health Information Cyber Security Framework (ADHICS) and Dubai Health Authority (DHA) cybersecurity guidelines, safeguarding patient data and maintaining secure digital healthcare environments across the region.
Digital Forensics and Incident Response services offer comprehensive solutions for investigating cybersecurity incidents, collecting, and analyzing digital evidence, and implementing effective response strategies to contain risks and minimize impact. These services leverage advanced techniques and technologies to identify, contain, and remediate security breaches swiftly and efficiently. Additionally, we also provide technical reports which is a mandate from a service provider such as us to be presented to the police, court, and all legal authorities.
In today's data-driven world, safeguarding sensitive information and intellectual property is critical to maintaining the trust and integrity of businesses. We recognize the importance of data security in preserving the confidentiality, integrity, and availability of valuable data assets.
Our comprehensive approach to data security encompasses a range of sophisticated solutions tailored to address the diverse needs of modern organizations.
By implementing Data Loss Prevention (DLP) solutions and advanced data classification techniques, we help organizations identify and categorize their data assets based on their sensitivity levels, enabling granular control and protection measures to be applied where they are needed most. Through encryption technologies, we ensure that data remains protected both in transit and at rest, mitigating the risk of unauthorized access or interception.
Additionally, using Digital Rights Management (DRM) solutions we can control and manage access to the digital content, ensuring that sensitive information remains protected regardless of its distribution or usage. By leveraging these comprehensive security measures alongside proactive monitoring and detection mechanisms, we empower organizations to stay ahead of evolving data security threats and maintain compliance with regulatory requirements.
Together, we can fortify defenses, mitigate risks, and safeguard sensitive information and intellectual property assets with unparalleled expertise and dedication
Our dedicated team is committed to providing you with prompt and personalized support. Feel free to reach out to us, and we'll get back to you as soon as possible.

